透過Nginx搭配Naxsi來實現WAF(Web Application Firewall)
Naxsi是一个open source Nginx WAF module,Naxsi的主要目標是包護Web APP,防止SQL injection、XXC、本地和遠端文件的漏洞等等...
Naxsi 不需要依賴類似防毒軟體的病毒碼資料庫,因此不會被未知攻集模式忽略(就像我們平常说的主動防御)
Naxsi 和其他 WAF 之間的另一个主要差異就是只偵測 http GET 和 POST
因為本身算是Nainx的一個模組,所以建議使用tarball安裝Nginx並且自行編譯
1. 先安裝必要套件
yum groupinstall "development tools" -y
2. 安裝PCRE以及open ssl套件
yum install pcre pcre-devel openssl openssl-devel -y
3. 下載nginx以及naxsi (這邊用nginx 1.12版搭配最新的naxsi)
git clone https://github.com/nbs-system/naxsi.git
wget http://nginx.org/download/nginx-1.12.1.tar.gz
useradd -s /sbin/nologin -M nginx
tar xf nginx-1.12.1.tar.gz
cd nginx-1.12.1
4. 編譯nginx,參數最重要就是記得--add-module把naxsi指定進去,其他看個人喜好
./configure --prefix=/usr/local/nginx --user=nginx --group=nginx --with-http_ssl_module --add-module=../naxsi/naxsi_src/
make && make install
5. 將Naxsi主要設定檔複製進Nginx conf中 (假設Naxsi下載在/root)
cp /root/naxsi/naxsi_config/naxsi_core.rules /usr/local/nginx/conf/
6. 修改nginx.conf,加入Naxsi模組在http區塊
http {
include /usr/local/nginx/conf/naxsi_core.rules;
}
7. 建立網站防護規則
vi /usr/local/nginx/conf/naxsi.rules
SecRulesEnabled; # 啟用naxsi
# LearningMode; # 是否啟用學習模式,只紀錄,不阻擋,方便設定白名單
DeniedUrl "/RequestDenied";
CheckRule "$SQL >= 8" BLOCK;
CheckRule "$RFI >= 8" BLOCK;
CheckRule "$TRAVERSAL >= 4" BLOCK;
CheckRule "$EVADE >= 4" BLOCK;
CheckRule "$XSS >= 8" BLOCK;
error_log /var/log/naxsi_attach.log;
8. 將網站規則加入web root
server {
... 省略
location / {
include /usr/local/nginx/conf/naxsi.rules;
... 省略
}
... 省略
}
9. 增加並修改 /RequextDenied error 400頁面
server {
... 省略
location /RequestDenied {
return 400;
}
error_page 400 /err-400.htm
}
vim /usr/local/nginx/html/err-400.html
<html lang="en">
<head>
<!-- Simple HttpErrorPages | MIT X11 License | https://github.com/AndiDittrich/HttpErrorPages -->
<meta charset="utf-8" />
<meta http-equiv="X-UA-Compatible" content="IE=edge" />
<meta name="viewport" content="width=device-width, initial-scale=1" />
<title>We've got some trouble | 400 - Bad Request</title>
<style type="text/css">/*! normalize.css v5.0.0 | MIT License | github.com/necolas/normalize.css */html{font-family:sans-serif;line-height:1.15;-ms-text-size-adjust:100%;-webkit-text-size-adjust:100%}body{margin:0}article,aside,footer,header,nav,section{display:block}h1{font-size:2em;margin:.67em 0}figcaption,figure,main{display:block}figure{margin:1em 40px}hr{box-sizing:content-box;height:0;overflow:visible}pre{font-family:monospace,monospace;font-size:1em}a{background-color:transparent;-webkit-text-decoration-skip:objects}a:active,a:hover{outline-width:0}abbr[title]{border-bottom:none;text-decoration:underline;text-decoration:underline dotted}b,strong{font-weight:inherit}b,strong{font-weight:bolder}code,kbd,samp{font-family:monospace,monospace;font-size:1em}dfn{font-style:italic}mark{background-color:#ff0;color:#000}small{font-size:80%}sub,sup{font-size:75%;line-height:0;position:relative;vertical-align:baseline}sub{bottom:-.25em}sup{top:-.5em}audio,video{display:inline-block}audio:not([controls]){display:none;height:0}img{border-style:none}svg:not(:root){overflow:hidden}button,input,optgroup,select,textarea{font-family:sans-serif;font-size:100%;line-height:1.15;margin:0}button,input{overflow:visible}button,select{text-transform:none}[type=reset],[type=submit],button,html [type=button]{-webkit-appearance:button}[type=button]::-moz-focus-inner,[type=reset]::-moz-focus-inner,[type=submit]::-moz-focus-inner,button::-moz-focus-inner{border-style:none;padding:0}[type=button]:-moz-focusring,[type=reset]:-moz-focusring,[type=submit]:-moz-focusring,button:-moz-focusring{outline:1px dotted ButtonText}fieldset{border:1px solid silver;margin:0 2px;padding:.35em .625em .75em}legend{box-sizing:border-box;color:inherit;display:table;max-width:100%;padding:0;white-space:normal}progress{display:inline-block;vertical-align:baseline}textarea{overflow:auto}[type=checkbox],[type=radio]{box-sizing:border-box;padding:0}[type=number]::-webkit-inner-spin-button,[type=number]::-webkit-outer-spin-button{height:auto}[type=search]{-webkit-appearance:textfield;outline-offset:-2px}[type=search]::-webkit-search-cancel-button,[type=search]::-webkit-search-decoration{-webkit-appearance:none}::-webkit-file-upload-button{-webkit-appearance:button;font:inherit}details,menu{display:block}summary{display:list-item}canvas{display:inline-block}template{display:none}[hidden]{display:none}/*! Simple HttpErrorPages | MIT X11 License | https://github.com/AndiDittrich/HttpErrorPages */body,html{width:100%;height:100%;background-color:#21232a}body{color:#fff;text-align:center;text-shadow:0 2px 4px rgba(0,0,0,.5);padding:0;min-height:100%;-webkit-box-shadow:inset 0 0 75pt rgba(0,0,0,.8);box-shadow:inset 0 0 75pt rgba(0,0,0,.8);display:table;font-family:"Open Sans",Arial,sans-serif}h1{font-family:inherit;font-weight:500;line-height:1.1;color:inherit;font-size:36px}h1 small{font-size:68%;font-weight:400;line-height:1;color:#777}a{text-decoration:none;color:#fff;font-size:inherit;border-bottom:dotted 1px #707070}.lead{color:silver;font-size:21px;line-height:1.4}.cover{display:table-cell;vertical-align:middle;padding:0 20px}footer{position:fixed;width:100%;height:40px;left:0;bottom:0;color:#a0a0a0;font-size:14px}</style>
</head>
<body>
<div class="cover">
<h1>Bad Request <small>Error 400</small></h1>
<p class="lead">The server cannot process the request due to something that is perceived to be a client error.</p>
</div>
</body>
</html>
10. 檢查設定檔並啟動nginx
/usr/local/nginx/sbin/nginx -t && /usr/local/nginx/sbin/nginx
11. 測試防禦
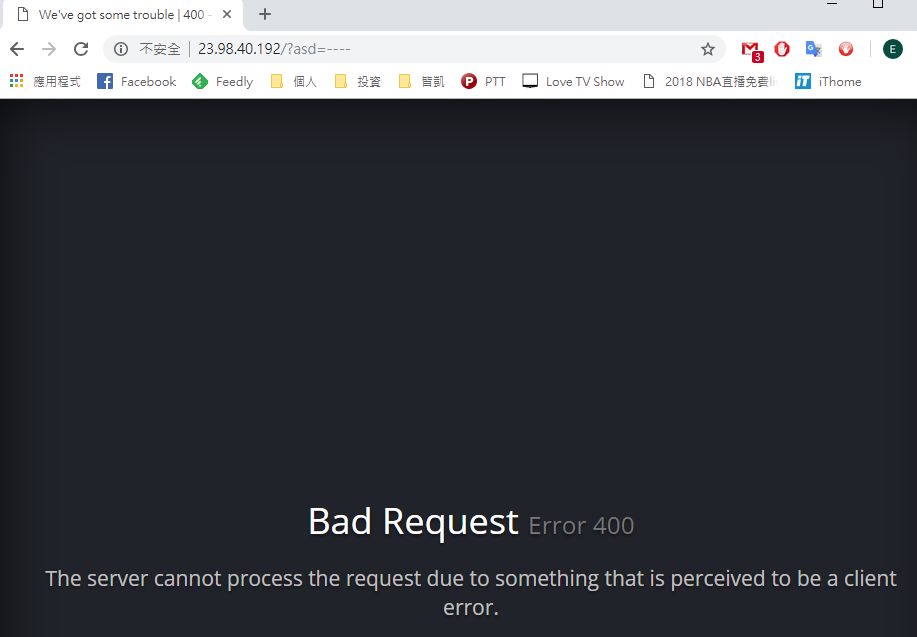
A. 使用SQL註解符號「--」 http://url/?asd=---
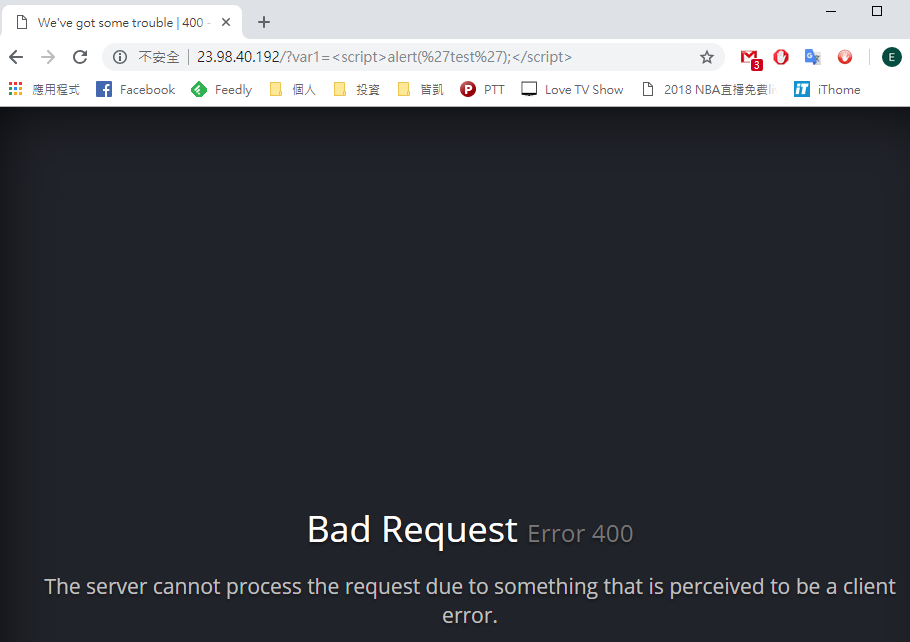
B. 使用XSS http://url/?var1=<script>alert('test');</script>
12. Log 分析
tailf /var/log/naxsi_attach.log
省略部分內容...
NAXSI_FMT: block=1&cscore0=$SQL&score0=12&zone0=ARGS&id0=1007&var_name0=asd,server: localhost, request: "GET /?asd=---- HTTP/1.1"
NAXSI_FMT: block=1&cscore0=$SQL&score0=4&cscore1=$XSS&score1=8&zone0=ARGS&id0=1008&var_name0=var1,server: localhost, request: "GET /?var1=%3Cscript%3Ealert(%27test%27);%3C/script%3E HTTP/1.1"
第一行 : 「block=1」表示已阻擋該次訪問,該次訪問是以「$SQL」來判斷。此次的分數總計達12分,已超過設定分數(8分)
第二行 : 「block=1」表示已阻擋該次訪問,該次訪問是以「$XSS」來判斷。此次的分數總計達8分,剛好符合設定的阻擋分數(8分)